Realme 7 (RMX2151) Remove Realme ID One Clıck With by Hydra

=====================================
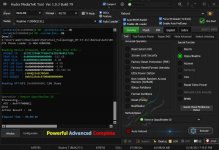
Searching for MTK Device... Found
Port Identification : Flashmode BROM
FriendlyName : MediaTek USB Port (COM1)
Device : 5&7cbc383&0&1
SymbolicName :??USB#VID_0E8D&PID_0003#5&7cbc383&0&1#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Driver Ver : 08/03/2016,3.0.1504.0
Opened handle..
Handshaking... Ok
Identifying Hardware ID.....
Reading Device hardware info..
hw code : 0813 MT6785 [6785]
hw subcode : 8A00
hw version : CA00
sw version : 0000
Target config : E5
SBC : 01 (True)
SLA : 00 (False)
DAA : 04 (True)
SWJTAG : 04 (True)
EPP : 00 (False)
CERT : 00 (False)
MEMREAD : 20 (True)
MEMWRITE : 40 (True)
CMD_C8 : 80 (True)
Exploiting Device...
Exploit Sent..
Successfully Exploited...
Handshaking... Ok
--- ENABLE AUTO PREL DUMP ----
Found
C:UsersambroDownloadsHydraTool_Fullpackage_07-17-21BackupPreloader_dumpprel.tmp
------------------------------
Handshaking...
Identifying Hardware ID.....
Reading Device hardware info..
hw code : 0813 MT6785 [6785]
hw subcode : 8A00
hw version : CA00
sw version : 0000
Target config : 00
SBC : 00 (False)
SLA : 00 (False)
DAA : 00 (False)
SWJTAG : 00 (False)
EPP : 00 (False)
CERT : 00 (False)
MEMREAD : 00 (False)
MEMWRITE : 00 (False)
CMD_C8 : 00 (False)
MEID : 956EF97C2E448984F6B27E17C72264C4
Stage 1.. [Size:234968]
Sending : Please wait.. Accepted
Identifying Protocol...
Protocol : New
Synchronization... SYNC
Preloader Initialization...
sing prel.tmp
Init : Accepted
Executing : SYNC
Reading Device UniqueID, RAM and Flash Chip Info...
UNIQUE ID : 6CC81729A0C7F68A7563553B68E17326
ERAM Size : 0x0000000000080000 -512 KB
IRAM Size : 0x0000000180000000 -6 GB
UFS LU0 Size: 0x0000000000400000 -4 MB
UFS LU1 Size: 0x0000000000400000 -4 MB
UFS LU2 Size: 0x0000000EE5800000 -59.586 GB
UFS CID : -'01H9HQ53AECMMDAR
UFS UNIQID : 0db9228e8c07000000000000
Executing : ACCEPTED...
Reading GPT0 -UFS [0x00008000] 0 130 Items
0
Autobackup titions
-preloader [0x00000000] 512 KB -> preloader.bin... Ok0
-> Renaming Preloader.... preloader_oppo6785.bin0
Creating Scatter file... C:UsersambroDownloadsHydraTool_Fullpackage_07-17-21BackupAuto0813__122821191922MT6785_Android_scatter.txt
-pgpt [0x00000000] 32 KB -> pgpt.bin... Ok
-frp [0x0BE08000] 1024 KB -> frp.bin... Ok
-nvdata [0x0F708000] 64 MB -> nvdata.bin... Ok
-persist [0x16DA2000] 50.367 MB -> persist.bin... Ok
-protect1 [0x1A000000] 8 MB -> protect1.bin... Ok
-protect2 [0x1A800000] 8 MB -> protect2.bin... Ok
-nvram [0x1ED00000] 64 MB -> nvram.bin... Ok
Done!!!0
C:UsersambroDownloadsHydraTool_Fullpackage_07-17-21BackupAuto0813__122821191922
MTK Phone Loader is NOW RUNNING.
Reading Device UniqueID, RAM and Flash Chip Info...
UNIQUE ID : 1 6CC81729A0C7F68A7563553B68E17326
ERAM Size : 1 0x0000000000080000 -512 KB
IRAM Size : 1 0x0000000180000000 -6 GB
UFS LU0 Size: 0x0000000000400000 -4 MB
UFS LU1 Size: 0x0000000000400000 -4 MB
UFS LU2 Size: 0x0000000EE5800000 -59.586 GB
UFS CID : -'01H9HQ53AECMMDAR
UFS UNIQID : 0db9228e8c07000000000000
Reading GPT0 -UFS [0x00008000] 0 130 Items
-------------------------------------
Operation : Remove Oppo/Realme ID
Processing...
ACK : 0xFFFF0000[]
Done
Action Result : 0 Ok
Elapsed Time : 00:00:40