SHERIF
Profesyonel Teknik Servis
Staff member
Admin
Co-Admin
WebMaster
Premium Üye
Destek Ekibi
GSM Expert
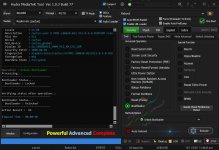
Redmi 6A (cactus) Bootloader Unlock With by Hydra

=====================================
Searching for MTK Device... Found
Port Identification : Flashmode BROM
FriendlyName : MediaTek USB Port_V1633 (COM42)
Device : 5&201b4142&0&4
SymbolicName :??USB#VID_0E8D&PID_0003#5&201b4142&0&4#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Driver Ver : 01/22/2015,3.0.1504.0
Opened handle..
Handshaking... Ok
Identifying Hardware ID.....
Reading Device hardware info..
hw code : 0766 MT6765 [6765]
hw subcode : 8A00
hw version : CA00
sw version : 0000
Target config : E7
SBC : 01 (True)
SLA : 02 (True)
DAA : 04 (True)
SWJTAG : 06 (True)
EPP : 00 (False)
CERT : 00 (False)
MEMREAD : 20 (True)
MEMWRITE : 40 (True)
CMD_C8 : 80 (True)
Exploiting Device...
Exploit Sent..
Successfully Exploited...
Handshaking... Ok
Handshaking...
Identifying Hardware ID.....
Reading Device hardware info..
hw code : 0766 MT6765 [6765]
hw subcode : 8A00
hw version : CA00
sw version : 0000
Target config : 00
SBC : 00 (False)
SLA : 00 (False)
DAA : 00 (False)
SWJTAG : 00 (False)
EPP : 00 (False)
CERT : 00 (False)
MEMREAD : 00 (False)
MEMWRITE : 00 (False)
CMD_C8 : 00 (False)
MEID : FC9ADF630C7F4D269617DA0B05
Stage 1.. [Size:216440]
Sending : Please wait.. Accepted
Identifying Protocol...
Protocol : New
Synchronization... SYNC
Preloader Initialization...
sing preloader_cactus.bin
Init : Accepted
Executing : SYNC
Reading Device UniqueID, RAM and Flash Chip Info...
UNIQUE ID : BCACA78C61EAAA92740BC47B5D80D288
ERAM Size : 0x0000000000038000 -224 KB
IRAM Size : 0x0000000080000000 -2 GB
eMMC BOOT1 : 0x0000000000400000 -4 MB
eMMC BOOT2 : 0x0000000000400000 -4 MB
eMMC RPMB : 0x0000000000400000 -4 MB
eMMC USER : 0x00000003AB400000 -14.676 GB
eMMC CID : 90014A484147346132A54B48809A1671 - HAG4a2
Executing : ACCEPTED...
Reading GPT -EMMC [0x00008000] 130 Items
Reading System Info
Brand : xiaomi
Vendor : Xiaomi
Model : Redmi 6A
ID : PPR1.180610.011
SDK : 28
Release : 9
ABI : armeabi-v7a
CPU abilist : armeabi-v7a,armeabi
Locale : en-GB
Description : cactus-user 9 PPR1.180610.011 V11.0.9.0.PCBMIXM release-keys
Miui Ver : V11
Device : cactus
Mod_device : cactus_global
Display ID : SW_S98506AE1_V009_M13_XM_C3C_USR
Security Patch : 2020-08-01
Fingerprint : xiaomi/cactus/cactus:9/PPR1.180610.011/V11.0.9.0.PCBMIXM:user/release-keys
StorageType : mtp
Userdata State : Encrypted
Autobackup titions
-preloader [0x00000000] 512 KB -> preloader.bin...0 Ok
-> Renaming Preloader.... preloader_cactus.bin
Creating Scatter file... C:Hydra ToolBackupAuto0766_xiaomi_cactus_cactus_9_PPR1.180610.011_V11.0.9.0.PCBMIXM_111521114626MT6765_Android_scatter.txt
-pgpt [0x00000000] 32 KB -> pgpt.bin...0 Ok
-frp [0x05588000] 1024 KB -> frp.bin...0 Ok
-nvdata [0x07688000] 64 MB -> nvdata.bin...0 Ok
-protect1 [0x0D688000] 8 MB -> protect1.bin...0 Ok
-protect2 [0x0DE88000] 9.469 MB -> protect2.bin...0 Ok
-persist [0x0F000000] 64 MB -> persist.bin...0 Ok
-nvram [0x1BE80000] 64 MB -> nvram.bin...0 Ok
Done!!!
C:Hydra ToolBackupAuto0766_xiaomi_cactus_cactus_9_PPR1.180610.011_V11.0.9.0.PCBMIXM_111521114626
MTK Phone Loader is NOW RUNNING.
Reading Device UniqueID, RAM and Flash Chip Info...
UNIQUE ID : 1 BCACA78C61EAAA92740BC47B5D80D288
ERAM Size : 1 0x0000000000038000 -224 KB
IRAM Size : 1 0x0000000080000000 -2 GB
eMMC BOOT1 : 0x0000000000400000 -4 MB
eMMC BOOT2 : 0x0000000000400000 -4 MB
eMMC RPMB : 0x0000000000400000 -4 MB
eMMC USER : 0x00000003AB400000 -14.676 GB
eMMC CID : 90014A484147346132A54B48809A1671 - HAG4a2
Reading GPT -EMMC [0x00008000] 130 Items
Reading System Info
Brand : xiaomi
Vendor : Xiaomi
Model : Redmi 6A
ID : PPR1.180610.011
SDK : 28
Release : 9
ABI : armeabi-v7a
CPU abilist : armeabi-v7a,armeabi
Locale : en-GB
Description : cactus-user 9 PPR1.180610.011 V11.0.9.0.PCBMIXM release-keys
Miui Ver : V11
Device : cactus
Mod_device : cactus_global
Display ID : SW_S98506AE1_V009_M13_XM_C3C_USR
Security Patch : 2020-08-01
Fingerprint : xiaomi/cactus/cactus:9/PPR1.180610.011/V11.0.9.0.PCBMIXM:user/release-keys
StorageType : mtp
Userdata State : Encrypted
-------------------------------------
Operation : Unlock Bootloader
Processing...
-------------------------------
Bootloader Status...
Bootloader : Locked
-------------------------------
Verifying status after operation...
-------------------------------
Bootloader Status...
Bootloader : Unlocked
-------------------------------
Action Result : Ok
Elapsed Time : 00:00:50